Configure LDAP
You can use the Lightweight Directory Access Protocol (LDAP) for authentication into the system. Specify user roles by using group DNs for users who log in as the administrator, operator or as a viewer.
The system has only one admin user and one operator: LDAP users log in as either the admin or operator, they do not have their own private profiles.
When enabled, LDAP authentication is an alternative to the regular system usernames and passwords. You may still login as admin, operator or viewer using the passwords for those accounts. Furthermore, any LDAP users with the name admin, operator or viewer are ignored. The local accounts are used instead.
For security reasons, you should configure passwords for the local accounts. See Configure LDAP.
These instructions assume you have a pre-configured LDAP server. The server must support anonymous binding or have a special bind account with search access privileges. (Note that Active Directory does not support anonymous binding.)
LDAP referrals, restrictions and failovers are not supported.
To configure LDAP authentication for your Standalone VGA Grid:
- Login to the Admin panel as admin. See Connect to the Admin panel.
- Select the
Access passwords link in the Configuration menu; the password configuration page opens. - Scroll to the LDAP authentication section.
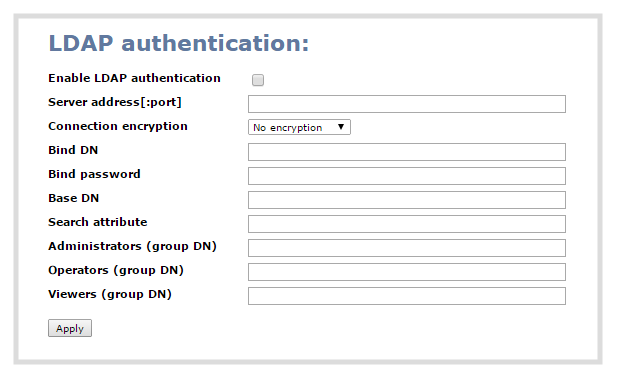
- Click the Enable LDAP authentication checkbox to enable LDAP authentication (or uncheck to disable).
- Specify the server IP address and (optional) port for your LDAP server (i.e. 192.168.1.101:389) in the Server address[:port] field.
- Use the Connection encryption drop-down to specify the type of encryption, if any used by your LDAP server.
| Connection encryption | Description/Default port used |
|---|---|
| No Encryption | No encryption is used to connect to the LDAP server. The default port is 389. |
| SSL | SSL encryption is used to connect to the LDAP server. The default port is 636. |
| TLS/STARTTLS | The connection is initially unencrypted then upgraded to TLS encryption is used. The default port is 389. |
- Specify the fully qualified DN and password for LDAP bind in the Bind DN and Bind password fields. (The password masked as dots on the screen.) These fields are only needed if your LDAP server does not support anonymous binding.
- In Base DN, specify the baseObject in which to search for entries. The system will search this object and the whole subtree starting at the base DN.
- By default the search attribute is uid, which is suitable for a unix environment. Specify a different value in the Search attribute field, if needed. For Active Directory environments, specify userPrincipalName. The value of this attribute must be unique in the Base DN.
- In the Administrators (group DN) field, specify the distinguished name of the group users must be part of to be logged in as the administrator. Users must have the member or unqueMember attribute for the specified group to be granted Administrator access.
If left blank, LDAP is not supported for Administrators (but can still be used for Operators and Viewers). - In the Operators (group DN) field, specify the distinguished name of the group users must be part of to be logged in as the operator. Users must have the member or unqueMember attribute for the specified group to be granted Operator access.
If left blank, LDAP is not supported for Operators (but can still be used for Administrators and Viewers). - In the Viewers (group DN) field, specify the distinguished name of the group users must be part of to be logged in as a viewer. Users must have the member or unqueMember attribute for the specified group to be granted Viewer access.
If left blank, LDAP is not supported for Viewers (but can still be used for Administrators and Operators). - Click Apply.
When a user of the LDAP server next visits the admin or viewer page for the system, the system prompts for use the username and password. For ActiveDirectory servers, the user needs to enter his fully qualified username (i.e. username@domainname) in addition to his LDAP password.
Users are required to authenticate once to the system and one time per channel they view. Therefore users see a prompt to log in to the system (the system name is shown) and a second time to log in to the channel (the channel name is shown).
In one case, LDAP replaces the local viewer account instead of working side-by-side with it.
When LDAP is enabled and the viewer account has no password (either there is no global viewer password or the channel overrides the global password with a blank password), the viewer must authentication with LDAP, he may not alternatively use the viewer account with a blank password.

