Implementing 802.1x network security on an enterprise network protects data and equipment from cyberattack. So what exactly is 802.1x?
The idea that someone could launch a cyberattack from within your corporate walls is real. That’s where the 802.1x network security protocol comes in to play.
802.1x network security provides protection from someone walking in, connecting a rogue device to your network and releasing a virus, malware, or a man-in-the-middle attack. Put another way, firewalls help protect from attacks originating outside the network and 802.1x helps protect from attacks originating within the network. It was originally designed to address wireless LAN access security concerns and was later adapted for wired LAN ports.
When you plug your laptop (or some other device) into a LAN port on a network with 802.1x, the device must prove to an Authentication Server that it’s allowed to connect. The Authentication Server communicates with your device using Extensible Authentication Protocol over LAN (EAPoL) and asks for credentials. All other forms of traffic coming from or going to your device is blocked. If your device doesn’t provide the right credentials, authentication fails and the device is unable to access the network.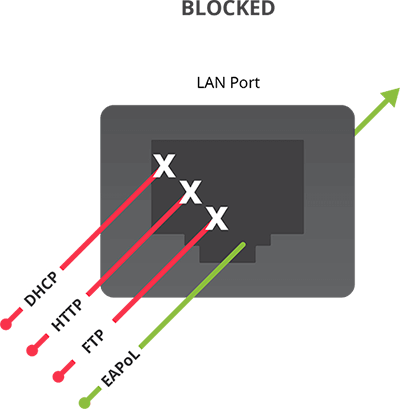
How does 802.1x authentication work?
Digital certificates are an essential part of 802.1x authentication. Certificates are shared, checked, and verified before any device is allowed to connect to the network. A secure channel is used during the negotiations, so all credentials are safe from prying eyes. If authentication validates, the LAN port opens and all traffic from that specific device is allowed access to the resources on the network.
The authentication flow goes something like this:
- The first thing the Authentication Server (AS) does when a device tries to connect to the network is it sends an encrypted digital certificate and its security key over EAPoL saying, “Trust me! I’m the AS in charge of this network.”
- The device takes the certificate and validates it using a public key from a trusted Certificate Authority. This step proves to the device that the AS really is who it says it is.
- Now that the device trusts that the AS is who it says it is, the AS needs to validate if the device is allowed to connect. To do this, a secure channel between the device and the AS is created and they negotiate authentication using the EAP access control method of that network.
Common access control methods
There are several access control methods commonly used by 802.1x:
- a user name and password (PEAP)
- a digital certificate for authentication (EAP-TLS)
- either a user name and password or a digital certificate (EAP-TTLS)
Does 802.1x network security benefit me?
802.1x network security keeps networks safe from cyberattacks while at the same time saves a bundle of time, money, and frustration when adding new gear to the network.
You don’t need a networking degree to connect equipment that’s 802.1x compliant. IT friendly gear can identify itself as a trusted device on the network and is a lot easier to deploy. Simply contact the IT guy and ask for the 802.1x network access method they’ve deployed and the current security certificate and/or password to get your gear on the network.
Wrap it up!
Not all equipment supports 802.1x network security, which is the case for a lot of AV equipment. Any piece of equipment you want to connect that does not support 802.1x requires MAB (MAC Authentication Bypass), which is a security risk that isn’t welcomed by IT network administrators.
Choosing an IT friendly live streaming encoder with built-in 802.1x network security makes connecting to enterprise networks easier, takes less time and effort to deploy, and won’t compromise network security. Look for AV gear with security features like 802.1x certificate authentication, RTMPS encryption of live streams, SFTP and HTTPS support for encrypted admin access.
Encoders like the Epiphan Pearl-2 and Pearl Mini all-in-one video switching, recording and streaming systems are 802.1x compliant and offer all the safety features you’d expect. They’re IT friendly, network secure and RTMPS ready. A great choice for lecture capture and live event recording.
For more details about the 802.1x implementation on our Pearl family of encoders, see this security white paper.
